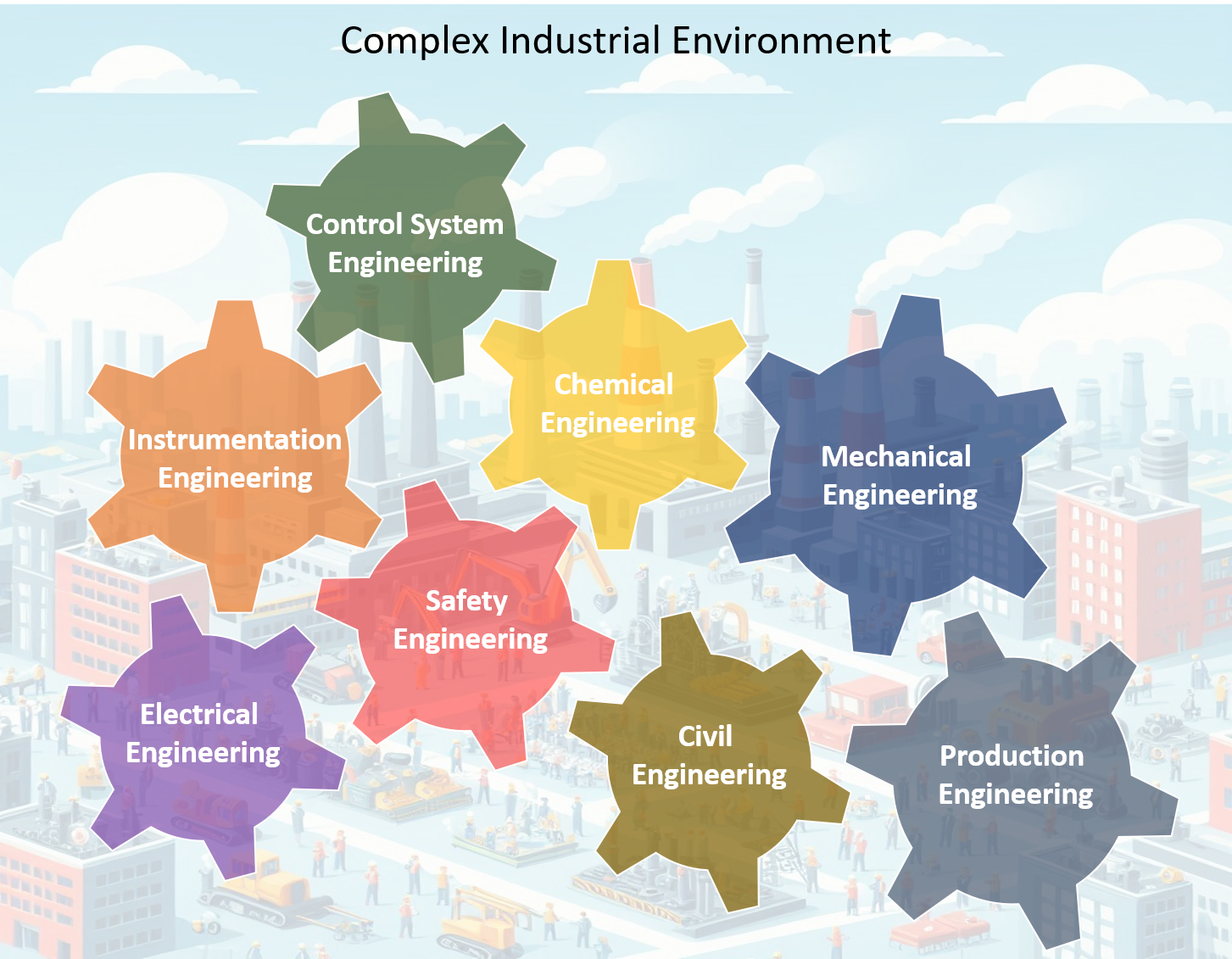
Amazon SageMaker’s Built-In Algorithms:
Linear Learner
Linear Learner combines the simplicity of linear models with the flexibility of gradient boosting algorithms. The algorithm automatically handles feature transformations and missing values, making it easy to use. It supports large datasets and can be trained quickly, making it suitable for real-time applications.
Use Cases:
Fraud detection: By training Linear Learner algorithm on historical data that includes both fraudulent and legitimate transactions, it can learn to classify new transactions as either fraudulent or legitimate. The algorithm can analyze various features of the transactions, such as transaction amount, location, and time, to make accurate predictions.
XGBoost
XGBoost can deal with both classification and regression problems. It is particularly useful when you have structured data with a large number of features. XGBoost is known for its ability to handle complex relationships between variables and its capability to handle missing values.
Use Cases:
Customer Churn Prediction
By training the algorithm on historical customer data, including factors such as demographics, purchase history, and customer interactions, it can learn to predict which customers are likely to churn or cancel their subscriptions. This information can help businesses take proactive measures to retain customers and improve customer satisfaction.
Anomaly detection
XGBoost can be used to identify unusual patterns or outliers in data. This can be applied in various domains such as fraud detection, network intrusion detection, or equipment failure prediction. By training the algorithm on normal data patterns, it can effectively identify deviations from the norm and flag potential anomalies.
Seq2Seq
Seq2Seq (Sequence-to-Sequence) can work with tasks that involve sequential data, such as language translation, text summarization, or speech recognition. It is specifically designed to handle problems where the input and output are both sequences of varying lengths.
Use Cases:
Machine Translation
By training the algorithm on pairs of sentences in different languages, it can learn to translate text from one language to another. For example, it can be used to translate English sentences into French or vice versa. The Seq2Seq algorithm is capable of capturing the contextual information and dependencies between words in a sentence, allowing it to generate accurate translations.
Text Summarization
By training the algorithm on pairs of long documents and their corresponding summaries, it can learn to generate concise summaries of text. This can be particularly useful in scenarios where there is a need to extract key information from lengthy documents, such as news articles or research papers.
DeepAR
DeepAR can be used when working with time series forecasting problems. It is specifically designed to handle tasks where the goal is to predict future values based on historical data.
Use Cases:
Demand Forecasting
By training the algorithm on historical sales data, it can learn to predict future demand for products or services. This can be particularly useful for businesses to optimize inventory management, production planning, and resource allocation.
Energy Load Forecasting
By training the algorithm on historical energy consumption data, it can learn to predict future energy demand. This can help utility companies optimize energy generation and distribution, as well as enable consumers to make informed decisions about energy usage.
Other Use Cases
The DeepAR algorithm is also applicable to other time series forecasting tasks such as stock market prediction, weather forecasting, and traffic flow prediction. It can capture complex patterns and dependencies in the data, making accurate predictions based on historical trends and seasonality.
BlazingText
BlazingText will help in text classification or natural language processing tasks. It is specifically designed to handle large-scale text data and can efficiently train models on massive datasets.
Use Cases:
Sentiment Analysis
By training the algorithm on a large corpus of text data labeled with sentiment (positive, negative, or neutral), it can learn to classify new text inputs based on their sentiment. This can be particularly useful for businesses to analyze customer feedback, social media posts, or product reviews to gain insights into customer sentiment and make data-driven decisions.
Document Classification
By training the algorithm on a diverse set of documents labeled with different categories, it can learn to classify new documents into relevant categories. This can be applied in various domains such as news categorization, spam detection, or topic classification.
Object2Vec
Object2Vec can be used with tasks that involve embedding and similarity analysis of objects or entities. It is specifically designed to handle scenarios where the goal is to learn meaningful representations of objects in a high-dimensional space.
Use Cases:
Recommendation Systems
By training the algorithm on user-item interaction data, it can learn to generate embeddings for users and items. These embeddings can then be used to calculate similarity scores between users and items, enabling personalized recommendations. For example, in an e-commerce setting, the algorithm can learn to recommend products to users based on their browsing and purchase history.
Document Similarity Analysis
By training the algorithm on a collection of documents, it can learn to generate embeddings for each document. These embeddings can be used to measure the similarity between documents, enabling tasks such as document clustering or search result ranking.
Other Use Cases
The Object2Vec algorithm is also applicable to tasks such as image similarity analysis, fraud detection, and anomaly detection. It can learn meaningful representations of objects or entities, allowing for efficient comparison and identification of similar instances.
Object Detection
Object Detection can help in detecting and localizing objects within images or videos. It is specifically designed to handle scenarios where the goal is to identify and locate multiple objects of interest within an image or video frame.
Use Cases:
Autonomous Driving
By training the algorithm on a dataset of labeled images or videos, it can learn to detect and localize various objects on the road, such as cars, pedestrians, traffic signs, and traffic lights. This can be crucial for developing advanced driver assistance systems (ADAS) or autonomous vehicles, enabling them to perceive and respond to their surroundings.
Inventory Management and Loss Prevention
By training the algorithm on images or videos of store shelves, it can learn to detect and locate products, ensuring accurate inventory counts and identifying instances of theft or misplaced items.
Other Use Cases
The Object Detection algorithm is also applicable to tasks such as surveillance, object tracking, and medical imaging. It can detect and localize objects of interest within complex scenes, providing valuable insights and enabling automated analysis.
Image Classification
Image Classification can categorize images into different classes or labels. It is specifically designed to handle scenarios where the goal is to classify images based on their visual content.
Use Cases:
Medical Imaging
By training the algorithm on a dataset of labeled medical images, it can learn to classify images into different categories such as normal or abnormal, or specific medical conditions. This can assist healthcare professionals in diagnosing diseases, identifying abnormalities, and making informed treatment decisions.
Product Categorization
By training the algorithm on a dataset of labeled product images, it can learn to classify images into different categories such as clothing, electronics, or home goods. This can help automate the process of organizing and categorizing products, improving search and recommendation systems for online retailers.
Other Use Cases
The Image Classification algorithm is also applicable to tasks such as facial recognition, object recognition, and quality control in manufacturing. It can accurately classify images based on their visual features, enabling a wide range of applications in various industries.
Semantic Segmentation
Semantic Segmentation can do pixel-level segmentation of images. It is specifically designed to handle scenarios where the goal is to assign a class label to each pixel in an image, thereby segmenting the image into meaningful regions.
Use Cases:
Autonomous Driving
By training the algorithm on a dataset of labeled images, it can learn to segment the images into different classes such as road, vehicles, pedestrians, and buildings. This can be crucial for developing advanced driver assistance systems (ADAS) or autonomous vehicles, enabling them to understand and navigate their environment.
Medical Imaging
By training the algorithm on a dataset of labeled medical images, it can learn to segment the images into different anatomical structures or regions of interest. This can assist healthcare professionals in accurate diagnosis, treatment planning, and surgical interventions.
Other Use Cases
The Semantic Segmentation algorithm is also applicable to tasks such as object detection, scene understanding, and image editing.
Random Cut Forest
Random Cut Forest (RCF) can do anomaly detection in high-dimensional data. It is specifically designed to handle scenarios where the goal is to identify unusual patterns or outliers within a dataset.
Use Cases:
Fraud Detection
By training the algorithm on a dataset of normal transactions, it can learn to identify anomalous transactions that deviate from the normal patterns. This can help businesses detect fraudulent activities, such as credit card fraud or money laundering, and take appropriate actions to mitigate risks.
Cybersecurity
By training the algorithm on a dataset of normal network traffic patterns, it can learn to detect abnormal network behaviors that may indicate a cyber attack or intrusion. This can help organizations identify and respond to security threats in real-time, enhancing their overall cybersecurity posture.
Other Use Cases
Random Cut Forest algorithm can also be used for tasks such as equipment failure prediction, sensor data analysis, and quality control in manufacturing. It can effectively identify anomalies or outliers within high-dimensional data, enabling proactive maintenance, process optimization, and early detection of potential issues.
Neural Topic Model
Neural Topic Model algorithm is specifically designed for topic modeling tasks, which involve discovering latent topics within a collection of documents. It utilizes a neural network-based approach to learn the underlying structure and relationships between words and topics in the text data.
Use Cases:
Content Analysis and Recommendation Systems
By training the algorithm on a large corpus of documents, it can learn to identify and extract meaningful topics from the text. This can be useful for organizing and categorizing large document collections, enabling efficient search and recommendation systems.
Market Research and Customer Feedback Analysis
By training the algorithm on customer reviews, surveys, or social media data, it can uncover the main topics and themes discussed by customers. This can provide valuable insights into customer preferences, sentiment analysis, and help businesses make data-driven decisions.
Latent Dirichlet Allocation – LDA
LDA can help in topic modeling. It is specifically designed to uncover latent topics within a collection of documents and assign topic probabilities to each document.
Use Cases:
Text Mining and Document Clustering
By training the algorithm on a dataset of documents, it can learn to identify the underlying topics present in the text. This can be useful for organizing and categorizing large document collections, enabling efficient search, recommendation systems, or content analysis.
Social Media Analysis and Sentiment Analysis
By training the algorithm on social media posts or customer reviews, it can uncover the main topics being discussed and analyze the sentiment associated with each topic.
Other Use Cases
The LDA algorithm is also applicable to tasks such as information retrieval, document summarization, and content recommendation. It can uncover the hidden thematic structure within text data, allowing for efficient organization, summarization, and retrieval of relevant information.
K Nearest Neighbors – KNN
KNN can help with both classification or regression tasks based on similarity measures. It is specifically designed to handle scenarios where the goal is to predict the class or value of a new data point based on its proximity to its neighboring data points.
Use Cases:
Recommendation Systems
By training the algorithm on a dataset of user-item interactions, it can learn to predict user preferences or recommend items based on the similarity of users or items. This can be useful for personalized recommendations in e-commerce, content streaming platforms, or social media.
Anomaly Detection
By training the algorithm on a dataset of normal data points, it can learn to identify anomalies or outliers based on their dissimilarity to the majority of the data. This can be applied in various domains such as fraud detection, network intrusion detection, or equipment failure prediction.
Other Use Cases
The KNN algorithm is also applicable to tasks such as image recognition, text classification, and customer segmentation. It can classify or predict based on the similarity of features or patterns, making it suitable for a wide range of applications.
K-Means
K-Means can work with tasks that involve clustering or grouping similar data points together. It is specifically designed to handle scenarios where the goal is to partition data into K distinct clusters based on their similarity.
Use Cases:
Customer Segmentation
By training the algorithm on customer data, such as demographics, purchase history, or browsing behavior, it can learn to group customers into distinct segments based on their similarities. This can help businesses tailor marketing strategies, personalize recommendations, or optimize customer experiences based on the characteristics of each segment.
Image Compression or Image Recognition
By training the algorithm on a dataset of images, it can learn to group similar images together based on their visual features. This can be useful for tasks such as image compression, where similar images can be represented by a single representative image, or for image recognition, where images can be classified into different categories based on their similarities.
Other Use Cases
K-Means can also help with document clustering, anomaly detection, and market segmentation. It can group data points based on their similarity, allowing for efficient organization, analysis, and decision-making.
Principal Component Analysis – PCA
Principal Component Analysis (PCA) can do dimensionality reduction and feature extraction. It is designed to handle scenarios where the goal is to transform high-dimensional data into a lower-dimensional representation while preserving the most important information.
Use Cases:
Data Visualization
By applying PCA to a high-dimensional dataset, it can reduce the dimensionality of the data while retaining the most significant features. This allows for visualizing the data in a lower-dimensional space, making it easier to understand and interpret complex relationships or patterns.
Feature Extraction
By applying PCA to a dataset with a large number of features, it can identify the most informative features and create a reduced set of features that capture the most important information. This can be useful for improving the efficiency and performance of machine learning models by reducing the dimensionality of the input data.
Factorization Machines
Factorization Machines mainly work for recommendation systems, personalized marketing, or collaborative filtering. It is designed to handle scenarios where the goal is to predict user preferences or make recommendations based on interactions between users and items.
Use Cases:
Recommendation Systems
By training the algorithm on user-item interaction data, such as ratings or purchase history, it can learn to predict user preferences and make personalized recommendations. This can be useful for e-commerce platforms, content streaming services, or social media platforms to enhance user experiences and drive engagement.
Personalized Marketing
By training the algorithm on customer data, such as demographics, browsing behavior, or past purchases, it can learn to predict customer preferences and tailor marketing campaigns accordingly. This can help businesses deliver targeted advertisements, personalized offers, or product recommendations to individual customers, improving conversion rates and customer satisfaction.
Other Use Cases
Factorization Machines is also applicable to tasks such as click-through rate prediction, sentiment analysis, and fraud detection. It can capture complex interactions between features and make accurate predictions based on the learned factorization model.
IP Insights
IP Insights is a feature in Amazon SageMaker that provides IP address geolocation and threat intelligence. However, it is not a built-in algorithm in the traditional sense.
It is designed to provide information about the geographical location and potential threat level associated with an IP address. It leverages data from various sources to determine the country, city, and coordinates associated with an IP address. Additionally, it provides threat intelligence information, such as whether the IP address is associated with known malicious activities or has a high-risk reputation.
Use Cases:
Cybersecurity and Network security
By utilizing IP Insights, organizations can analyze incoming network traffic and identify potential threats based on the geolocation and threat intelligence associated with IP addresses. This can help in detecting and mitigating malicious activities, such as unauthorized access attempts or distributed denial-of-service (DDoS) attacks.
Targeted Marketing and Content Localization
By leveraging IP Insights, businesses can tailor their marketing campaigns or content based on the geographical location of website visitors or customers. This can enable personalized experiences, targeted advertisements, or region-specific content delivery.
Reinforcement Learning
Reinforcement Learning (RL) can be used for sequential decision-making and learning from interactions with an environment. It is specifically designed to handle scenarios where the goal is to optimize an agent’s actions to maximize a reward signal over time.
Use Cases:
Autonomous Robotics
By training the algorithm on simulated or real-world environments, it can learn to control robotic systems to perform complex tasks. This can include tasks such as object manipulation, navigation, or even playing games. RL enables the agent to learn from trial and error, improving its performance over time through exploration and exploitation of the environment.
Recommendation Systems
By training the algorithm on user interactions and feedback, it can learn to make personalized recommendations that maximize user engagement or satisfaction. This can be applied in various domains such as e-commerce, content streaming platforms, or online advertising, where the goal is to optimize user experiences and increase conversion rates.
Other Use Cases
The Reinforcement Learning algorithm is also applicable to tasks such as resource allocation, portfolio management, and energy optimization. It can learn to make optimal decisions in dynamic and uncertain environments, leading to efficient resource utilization, investment strategies, or energy consumption.